Status Recorder
Is this new stealer a fork of something we have seen before
Overview
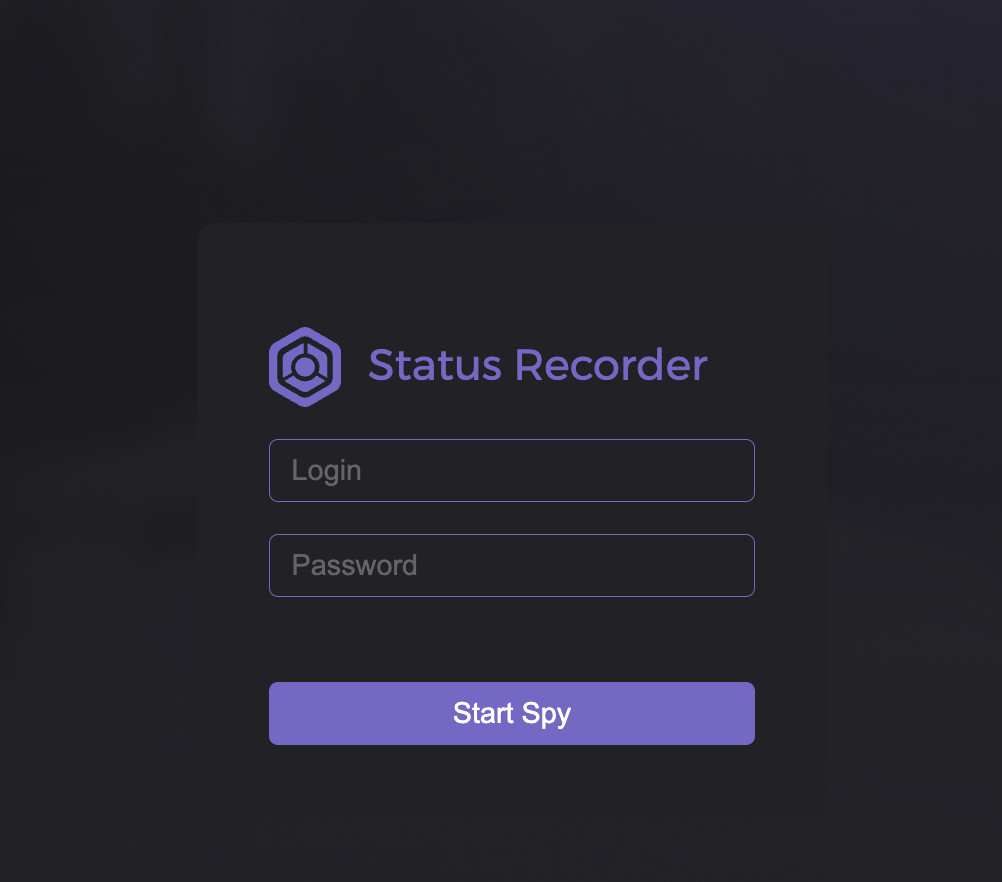
The name of this stealer is currently unknown but the C2 hosts a panel that is titled Status Recorder.
We first became aware of this from a tweet by @Jane_0sint tweet
UnkStealer🤷♀️ There is TitanStealer activity on these addresses, but the traffic structure and so on is very different from it. And the port is not 5000. 94.142.138[.]139 77.91.77[.]35 94.142.138[.]145 94.142.138[.]10 Ports:5001/5005https://app.any.run/tasks/0e933ce9-f531-401d-8d07-f518cdd9e2e1/
Following up @AnFam17 posted a tweet with a list of related hashes.
021db62d85d6e92e5c67fc9b06c87bf1
41f39df6d7243675e36805d9a591c350
39e7dc7f0cfa0ef6b646e794161d91a7
cc2f69864386e81eb527119f82713ccf
02398b35b4fa068d16806315eb423048
e22ef641c2d1600af204690c5ed50286
d9063ce4b74ca71cc661652603bca980
5acd73c4f3ee93180a7609a4d4458e91
f9b6aa6b0694cc878ed1cc0f7f4c9e63
f7b081d241439f7724222383473b1e2c
4573409d7e3578ecba9150cbf2158325
b0b7bbbc9e3dae849c750202db747f03
c03058303988c6f7992b38bda6804b9d
3d8e4db9f27659078528b3c69b6d6669
12ab2d4a70aefdb1dc7936518bc6258c
ebbfe27eddcaf5d651672aeb10c55302
f6f9457ba5ee5dcae89106b29b7f036a
14a8ec5c9448d6fecb58f04879237163
16f2a3898cdc27798158c9bf35a4eff4
d2cfc8672bcccb34f7f511901951494b
4587d9fde0fc6ad5decaaf9b391ebd5bPanel Hunt
Thanks to @LLxynLL we also have a nice google dork that can be used to hunt the panels.
intitle:"status recorder" intext:"start spy"Samples
-
032c59d8a9364ce30ded3ef4aa5cd6b6d632d1fcd994c03de02088db247e7d2dpacked-
7cdae8e3531a0ad631e07f351cb485065a697a147c431b5ddf97facfbfc10bf0unpacked
-
-
f476c1562bd503892b3219dff369a6f0a20eb667484237d380645d65dfd5a765packed-
830551aa368f53639f87284ec8bcdba971b8c58764154b5cdd54bd86ad5d1d72unpacked
-
Prior Research
@r0ny_123 found a potential link between StatusRecorder Erbium Stealer
- 41f39df6d7243675e36805d9a591c350 (StatusRecorder) @0x401a1e, @0x401aa3, @0x401b77
- 0541c00dc6b29c795cdc242f36e44ad6 (Erbium Stealer) @0x444639, @0x4446be, @0x4446be
Further investigation shows that these functions are dynamic API resolving using fnv1 (LoadLibraryA, GetProcAddress).
Also EmergingThreats created a snort rule for the traffic.
Analysis
Panel Analysis
Thanks to @__fastcall's over 1000000 hours on CSGO he noticed that the background from the panel is from CSGO! And @TheAifam5's sharp eyes found the exact scene!


Logo Overlap Coincidence
The stealer panel logo overlaps with a breach detection application. This could be a coincidence as other versions of the logo are used for unrelated applications but there are some interesting coincidences that we are going to investigate.

- Breach directory logo 1
- Breach directory application (modified logo)
- The breach directory developer has a github where he has multiple projects related to malware development including file binders and keyloggers.
- Interesting note he also commented on a CSGO cheat thread suggesting that he had built an injector for a CSGO cheat.
- Some of his github projects have been built and tested on ANYRUN giving us insight into his build path
C:\Users\rohan\Downloads\File-Binder-Pro-master\File-Binder-Pro-master\File-Binder-Pro-master\Dream AIO\obj\Debug\File Binder Pro.pdb
This is likely a coincidence we are just capturing this information on record until more data is found either confirming or refuting the link.
Malware Identification
C2 Traffic
The stolen data is exfiltrated using $$$$ keywords and the data itself is base64 encoded. This is a recursive structure.
$$$$$$WALLETS_START$$$$$$
JCQkJCRERVNLV0FMTEVUU19TVEFSVCQkJCQkCiQkJCQkREVTS1dBTExFVFNfRU5EJCQkJCQK
$$$$$$WALLETS_END$$$$$$
The C2 IP is hard coded in the binary 77.91.77.35$$$$ the $$$ appended to it is possibly as some type of obfuscation? The port is also hard coded in this case it is 5001. This is connected to via a raw TCP socket, the HTTP protocol is not used.
TitanStealer also uses this $$$ formatting but it could be coincidence A7DFB6BB7CA1C8271570DDCF81BB921CF4F222E6E190E5F420D4E1EDA0A0C1F2
.rdata:0051141C db 'tipodomain$$$$$$$$$$$$$$$$$'
.rdata:00511437 db 'installs$$$$$$$$$$$$$$$$$$$'
.rdata:00511452 db 'darkcorner$$$$$$$$$$$$$$$$$'PDB Path Hunting
5e72f0741d29914843c91b9daed3256c5c5e8c73f8a7cbfc20cb8a9c06775833
contains C:\Users\admin\source\repos\MemLoader\x64\Release\MemLoader.pdb
Yara Rule
rule StatusRecorder {
strings:
$s1 = "$$$$$$FILEGRABBER_FILE_" ascii
$s2 = "$$$$$$WALLETCORE_START$$$$$$" ascii
$s3 = "$$$$$$WALLETCORE_FILE_" ascii
$s4 = "$$$$$$WALLETCORE_END$$$$$$" ascii
$s5 = "$$$$$$WALLET_START_BINANCE$$$$$$" ascii
$s6 = "$$$$$BINANCE_FILE_" ascii
$s7 = "$$$$$$WALLET_END_BINANCE$$$$$$" ascii
$s8 = "$$$$$$WALLET_START_EXODUS$$$$$$" ascii
$s9 = "$$$$$EXODUS_FILE_" ascii
$s11 = "$$$$$$WALLET_END_EXODUS$$$$$$" ascii
$s12 = "$$$$$$WALLET_START_ATOMIC$$$$$$" ascii
$s13 = "$$$$$ATOMIC_FILE_" ascii
$s14 = "$$$$$$WALLET_END_ATOMIC$$$$$$" ascii
$s15 = "$$$$$$WALLET_START_ARMORY$$$$$$" ascii
$s16 = "$$$$$ARMORY_FILE_" ascii
$s17 = "$$$$$$WALLET_END_ARMORY$$$$$$" ascii
$s18 = "$$$$$$WALLET_START_COINOMI$$$$$$" ascii
$s19 = "$$$$$COINOMI_FILE_" ascii
$s20 = "$$$$$$WALLET_END_COINOMI$$$$$$" ascii
$s21 = "$$$$$$WALLET_START_ETHEREUM$$$$$$" ascii
$s22 = "$$$$$ETHEREUM_FILE_" ascii
$s23 = "$$$$$$WALLET_END_ETHEREUM$$$$$$" ascii
$s24 = "$$$$$$WALLET_START_ZCASH$$$$$$" ascii
$s25 = "$$$$$ZCASH_FILE_" ascii
$s26 = "$$$$$$WALLET_END_ZCASH$$$$$$" ascii
$s27 = "$$$$$$WALLET_START_JAXX$$$$$$" ascii
$s28 = "$$$$$JAXX_FILE_" ascii
$s29 = "$$$$$$WALLET_END_JAXX" ascii
$s30 = "GRABPATH_CONF$$$$$$$$$$$$$$$" ascii
$code = {558b ec8b 81 ?? ?? ?? ?? 85 c074 ?? 4033 d289 81 ?? ?? ?? ?? 85 c07e }
condition:
20 of ($s*) or
$code
}


